The download of Permission Analyzer is a zip file that can be unpacked anywhere. The application runs from the extracted directory and no installation is needed. Please note that Windows has additional restrictions on the “Program Files” directory and that Permission Analyzer can possibly only be run as an Administrator. To avoid these problems, it’s best that the application is extracted outside of the Program Files directory. To uninstall the application only the application folder needs to be deleted.
Permission Analyzer makes use of the Active Directory to retrieve additional member attributes that are not available from the file system, e.g. the displayName and (nested) group membership. The application’s scan screen will show specific Active Directory Organizational Units (OU) to be scanned and Permission Analyzer will limit the scan to those OUs. The scan will only search for items outside the OUs if they occur in the member or memberOf attributes of members in the OU. This is done to obtain a complete overview of group membership for each member of the OU(s).
Note: because a universal group can have members from domains other than the domain where the group object is stored and can be used to provide access to resources in any domain, only a global catalog server is guaranteed to have all universal group memberships that are required for authentication. On the other hand, the global catalog stores the membership (the member attribute) of only universal groups. The membership of other groups can be ascertained at the domain level. Therefore, if applicable, make sure you add both the domain controllers as your global catalogue to ensure a complete overview of group memberships. Permission Analyzer will make sure that no duplicate memberships are stored. Active Directory uses the following default ports:
- 389: LDAP without SSL
- 636: LDAP with SSL
- 3268: Global Catalog without SSL
- 3269: Global Catalog with SSL
- Go to the properties of Permission Analyzer.exe in Windows Explorer
- Go to the tab "Compatibility"
- Click the button "Change high DPI Settings"
- Check the checkbox at the bottom of the dialog to "Ignore DPI scaling" and select "System" in the dropdown box.
No, you can run Permission Analyzer from any server or workstation within your domain, as long as you have enough permissions to read the security properties of the directories to scan and the OUs in the Active Directory.
Permission Analyzer can easily be run from a workstation with a supplied database in the application folder. From the workstation different file servers can be scanned, just like the Active Directory for group information. In addition, you can use an extensive setup with scan agents and a central database to share information.
Instead of scanning a remote file system from a workstation, a Scan Agent can be used to perform a scan on the file server. Each Scan Agent will add the scanned information to the central database. A Scan Agent is a normal installation of Permission Analyzer but is activated with a cheaper Scan Agent license, with which only the scanning features of the application are activated. The progress and status messages of each Scan Agent can be viewed on, for example, a central workstation. A Scan Agent stores the status messages in the central database, which is also the way in which to communicate with an agent. Starting an agent can, as with the normal installation of Permission Analyzer, be scheduled via Windows Scheduled Tasks and application parameters such as scan.
See also the page How it works
Yes, the application can scan shares that support the NFSv4 ACL Model using the SMB protocol. Make sure ACL’s are enabled on the machine that hosts the network shares. For example, for OSX you can execute the following:
sudo defaults write /Library/Preferences/SystemConfiguration/com.apple.smb.server AclsEnabled -bool YES
In the Windows API (with some exceptions), the maximum length for a path is MAX_PATH, which is defined as 260 characters. Reading the file path is no problem, but getting the security descriptor of the file fails when the file path exceeds the MAX_PATH length. Permission Analyzer has a workaround to support long file paths anyway! Whenever necessary it converts the long file path to its 8.3 short notation (file names with ~1 etc) before reading the security properties. The long file path is stored in the database along with the security info retrieved by the short path. This way you still have a readable long path including the security info.
Access denied on the workspace directory
Permission Analyzer writes data into the directory where it has been installed. If the directory is located in Program Files, Windows may decide to block the writing operations of the application. If this is the case, run Permission Analyzer as an Administrator. Right click Permission Analyzer.exe and select Run as Administrator.
When performing a network scan a snapshot is made of the file system in combination with group information from the Active Directory. The database contains file names, access control entries and user and group information. The database also contains filters, reports, policies, which can be shared with several work stations by using a central database. The storage occupies approx. 1 MB per 1,000 directories/files.
The searches, reviews and reports in the “Report View” strictly use the database to show the results. The directories on the network and the Active Directory will only be accessed while running a network scan.
Yes, just move the files H2DB.h2.db and H2DB.trace.db to another location on your hard disk and change the database path in the settings of the application.
By default, the application uses a supplied H2 database which is included, in the form of a database file in the application directory. In the preferences in the application the following databases can also be used: Oracle, MSSQL, DB2, MySQL, PostgreSQL and Derby. By using an external database server the scanned information, reports, and filters can be shared between workstations, and potential Scan Agents can scan a local file system in parallel and save the information in the database. The application supports basically any database with a JDBC driver, contact support if the desired database is not listed. See the page on external database support for more information.
This depends a lot on the network performance, the file servers or local file system and whether or not an external database is used. Scanning local files with a local database scans about 25,000 files per minute and occupies 1 MB database storage per 1,000 files. As the database size increases the scanning speed drops, since with each new row the database needs to update a number of growing indexes.
Tip: use Scan Agents on the file servers to increase speed.
No, you can use an Internet connection to activate your license automatically, but you can also use our form on the website to create an offline activation file based on your license.
A dialog window can be opened within the application, allowing you to send a direct message to our tech support team. The dialog window also allows you to send the application log in zip format. Go to [Help] > [Contact support]. Make sure you’ve configured a valid SMTP server in the application settings before sending out the e-mail.
Yes, the recent version of Permission Analyzer has a number of new reports with which groups ‘unfolded’ in the HTML or CSV report are included. At this point the following report types can be selected:
- Folders/files and the sum of their permissions
- Folders/files and their Access Control List
- Folders/files and the ACL with expanded groups showing direct members and their effective permissions
- Folders/files and the ACL with expanded groups showing nested members and their effective permissions
- Users/groups and all their explicit permissions
- Groups and members
A list of directories and files that meet the filter criteria. Per directory, only the effective rights of all Access Control Entries that are found on the basis of the filters.
Instead of adding up all the rights, Access Control Entries (users and groups) are displayed separately per directory or file in this report.
Same as previous report type, but the report groups in the report popped up so that the direct group members are visible.
Same as the previous report type, but in addition to direct group members also the nested members of a group are displayed.
This report is laid down per user/group instead of directory/file. For each user or group the directories and explicit rights are displayed.
This report is separate from the rights and shows exclusively the groups found as well as their group members. A separate report type will only display the groups that actually have permissions in the (filtered) folder tree.
For more information, see also the page Reports.
The application supports exporting to HTML or CSV. A quick export can be done via the context menu of a directory or the Export button in the application toolbar. In order to create a periodic export a report can be used. A random set of filters can be saved as a new report. In a report, among other things, the file format, the destination path and the way of presenting are configured. A report can be loaded at any time in the application or be exported to HTML or CSV. See also the pages Reports and command-line parameters.
A set of filters can be saved as a new report, where the file path (with possible timestamp) can be configured per report. Using Windows Scheduled Tasks and different application parameters Permission Analyzer can be launched automatically, a scan can be run and reports can be exported. See command-line parameters.
Yes, group memberships are stored in the database during the network scan, from the Active Directory. The reviews show the standard rights of nested group memberships, these rights can be excluded with the check mark “Include group memberships” on the Members tab on the left of the outline. By unchecking this option the explicit rights of a user or group are displayed.
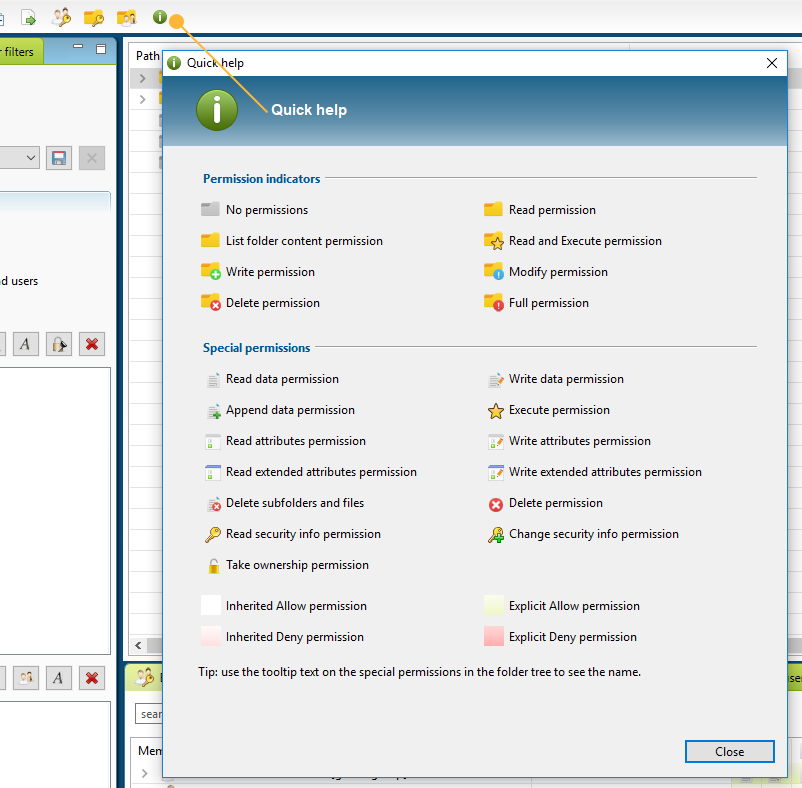
The folder tree should make it clear at a glance where the unwanted rights are and what rights are granted explicitly. The tree shows all rights per directory, initially this will mainly be FULL rights of the Administrators, but as more filters are applied, the tree will show the purposeful rights. The icon for the directory indicates which access right it involves. Press the green info icon in the toolbar to quickly get an overview of icons.
The icons to the right of the directories indicate which special rights apply to the directory (a summation of all Access Control Entries on the directory that match the filter criteria). The background color indicates whether these special rights are inherited from a parent folder (white background), or directly assigned to the directory (green background). A red background indicates a ‘Deny’ right.
Permission Analyzer provides a highly comprehensive collection of filters. The filters are divided into three categories, namely Members, Permissions and Folders. Each category can be found as a tab on the left of the outline. In the Member tab a list of users/groups can be added as an Include or Exclude keyword filter. That way only the rights for those users appears in the folder tree. It is even possible to select a group from which all members are included or excluded in the overview. The nested groups of each group member are included in the overview. This allows a quick bulk review to be done on a large group of users. The folder tree shows at a glance where the unwanted rights are. With the tabs at the bottom of the folder tree it’s possible to see which users have been found. The filters can be added as an Include filter or Exclude filter.
The Exclude filter on a username will only exclude that user from the overview. However, in order to show the directories to which a user has no rights, the nested group memberships of the outline should also be excluded. See following PDF for some simple steps to take to add the groups of a user as Exclude: Filter for folders not accessible by a particular user.pdf
A Permission Analyzer license is tied to one machine, either a server or a workstation. From one machine different servers can be scanned, multiple licenses apply to different workstations with an installation of Permission Analyzer, or in the case of Scan Agents (a cheaper license option) where Permission Analyzer is installed on each file server to run a local scan and add the information to a central database. You should select the appropriate edition of Permission Analyzer based on the number of groups and users you are scanning on the file system and Active Directory.
The edition of Permission Analyzer depends on the number of users and groups that is scanned in the Active Directory (the Organizational Units selected in the scan window of the application). The following list gives an indication of the edition that could apply:
- Basic: 1 file server / 500 users / 100 groups.
- Standard: 5 file servers / 3,000 users / 1,000 groups and support for encryption of the included (embedded) database supplied.
- Advanced: 15 file servers / 15,000 users / 5,000 groups and support for an external database such as MS SQL Server.
- Enterprise: Unlimited file servers, users and groups plus support for an external database such as MS SQL Server.
- Scan Agent: Suited for local scan of a single file server.
A license is linked to an installation of Permission Analyzer. That’s why it’s important to deactivate an old, previous installation. This can be done automatically online or manually through the website. Open [Help] > [License information] and select [Deactivate license]. You will now be able to activate the license on another device.
To request a quote, please fill out the form available on our website. Make sure to include all necessary details, including your VAT/Tax ID if applicable. Providing your VAT/Tax ID is essential for applying 0% tax for orders within the EU (and outside the Netherlands). If you have any questions, feel free to contact our support team for assistance!
Permission Analyzer’s orders are processed by our sales agent Paddle, one of the biggest software sales agents worldwide. Paddle supports lots of payment options, see https://www.paddle.com/help/start/intro-to-paddle/which-payment-methods-do-you-support. When you pay by credit card you will immediately receive the license file(s) by e-mail.
Sure! Just fill out our online form to request a trial license for a specific edition.

